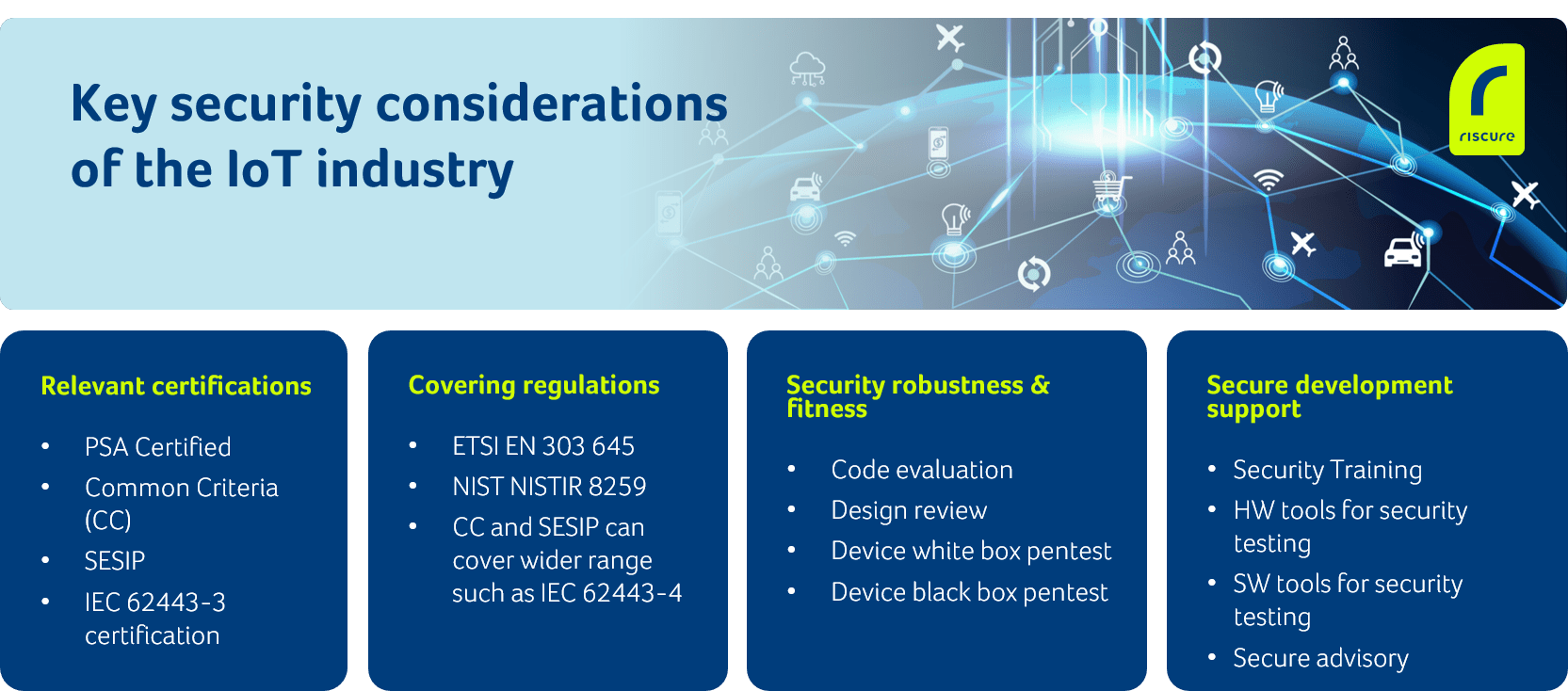
Security on the device level and network security go hand in hand. The security of devices with network connectivity, such as switches, routers, modems, and gateways, can influence the security of local as well as wider area networks. Riscure worked with many vendors and operators to test and demonstrate the security robustness of these IoT devices.
Next to traditional networks, 5G networks are quickly getting deployed, redefining device connectivity. In addition to the existing security challenges of a cellular network, any 5G development has to incorporate the emerging security aspects that concern Multi-access Edge Computing (MEC) services, lawful interception functionality, general availability of software and APIs to users. Often seen as the critical technology for economical well-being, 5G will also be integrated into adjacent industries such as automotive, where it uses V2X communication concepts.
Riscure has more than 20 years of experience in networking device security testing. Riscure also works together with Keysight, which offers our customers a combination of device testing tools and services, with device interfacing and network simulation tools.