Find vulnerabilities in embedded software earlier with True Code Static code checks and Dynamic Fault Injection simulation and Fuzzing.
True Code Highlights
Why we started it?
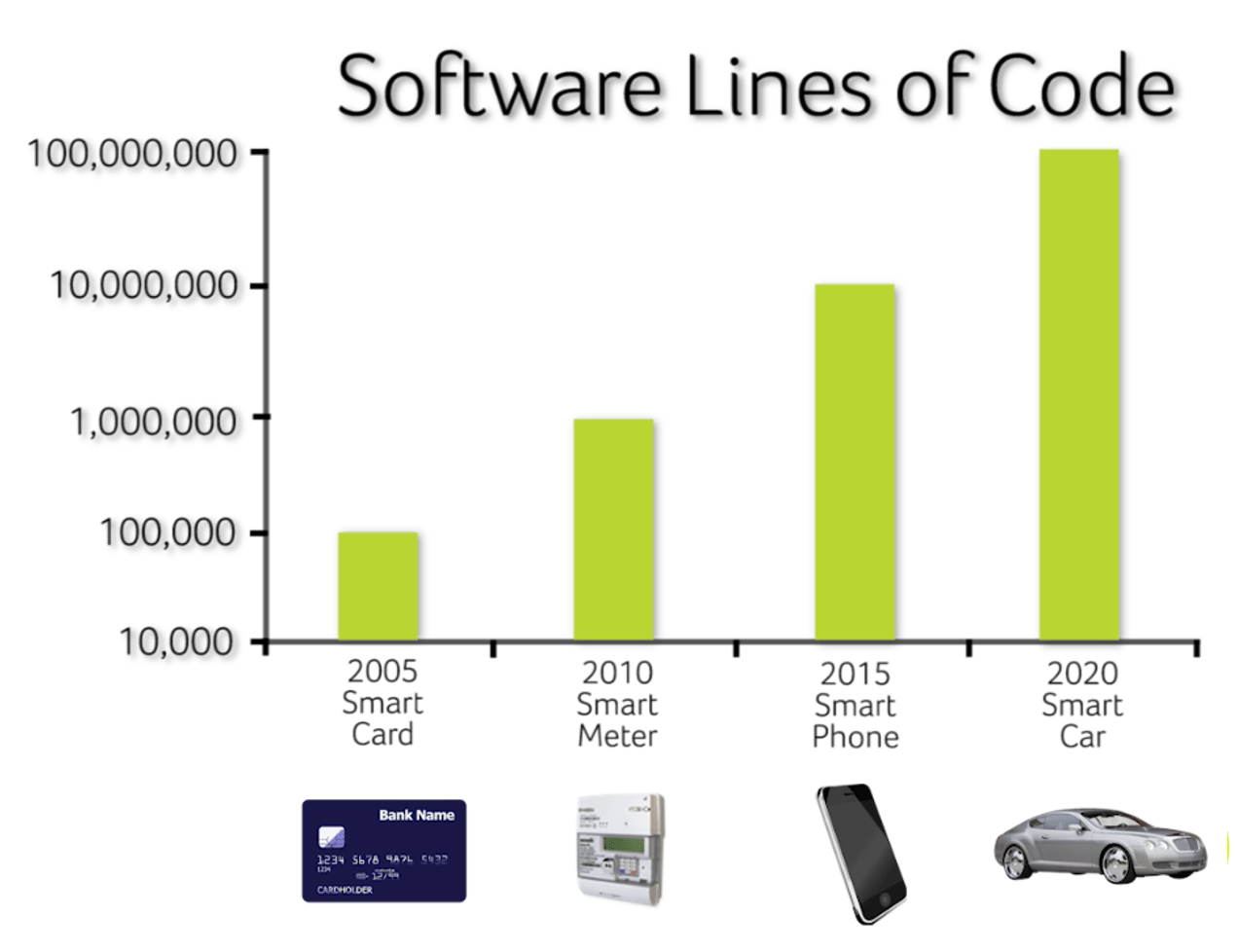
The size of software running on devices is constantly growing, which makes manual testing impractical. The attack surface for a potential hacker is getting larger (because of the larger codebase), so the likelihood of future exploits increases and, therefore, developers need to address the requirement for more testing. At the same time, general-purpose code checking tools often do not provide meaningful data. It is sometimes difficult to identify serious issues from minor coding errors. Meanwhile, research indicates that addressing a vulnerability during production can be over 100 times more expensive than identifying it during the design phase. To address these challenges, provide actionable security data and highlight serious security vulnerabilities specifically for embedded software, we developed Riscure True Code, a software testing solution for automating vulnerability identification in the SDLC and DevSecOps processes.
Automating security evaluation
Comprehensive automation capabilities
True Code will automatically check for vulnerabilities that are hard to prevent and find for a development team.
Integration
Embed code security check-up into your existing workflow.
Unique security insights
Obtain vulnerability data that no other tool offers.
Actionable data
Ensure response to security vulnerabilities from the development team during the design phase.
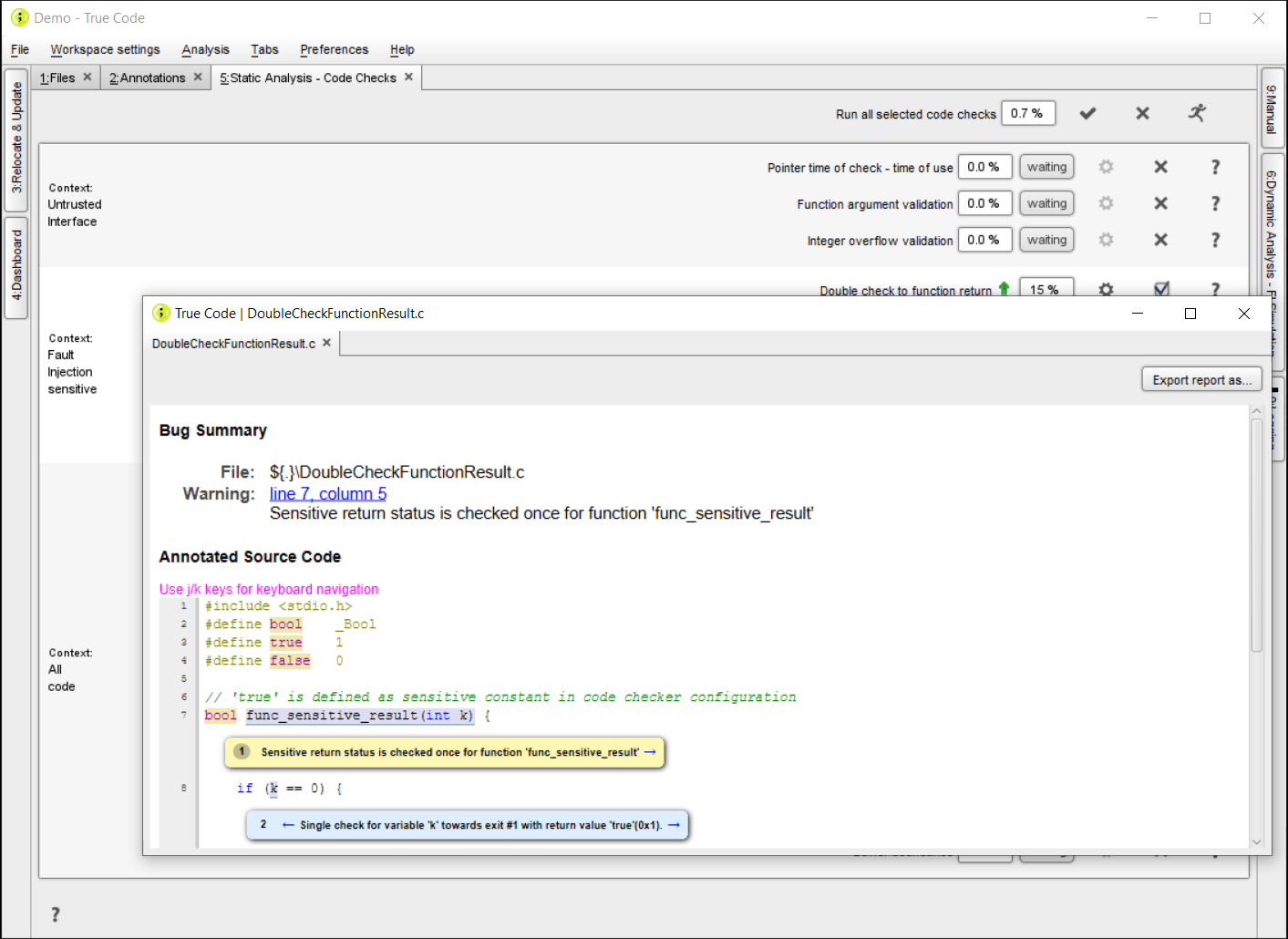
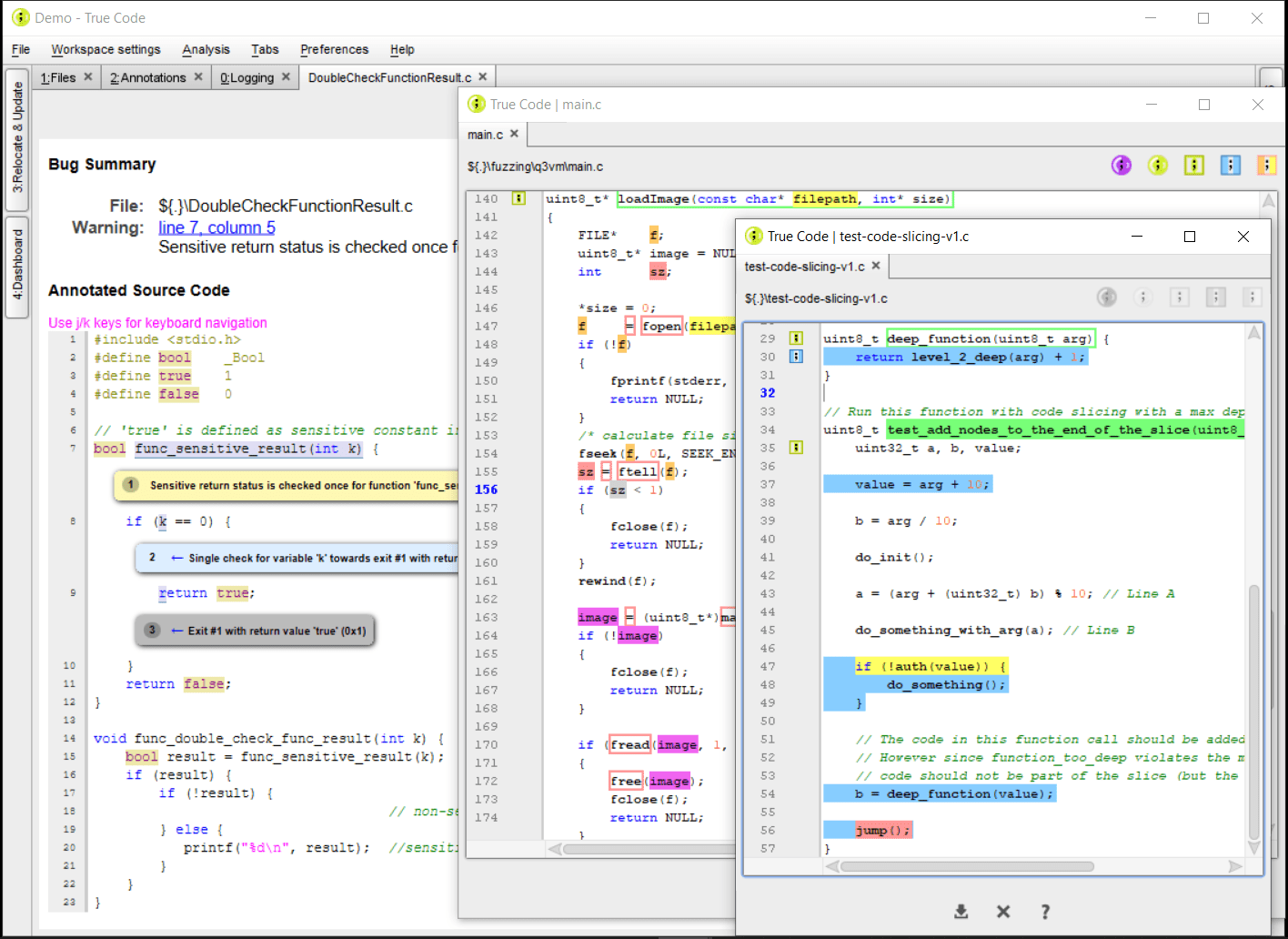
Static AnalysisOur Static Analysis module is a White Box testing method that provides all the logical static checks that can help you efficiently make the shift to the left. Especially for embedded software, we extended the list of static checks with all the checks that the Riscure Lab has developed over the last 2 decades: the Fault Injection sensitive checks are specific for situations where the software meets the hardware. Those can be performed with function-level granularity. It is fully compatible with code written in C. |
 |
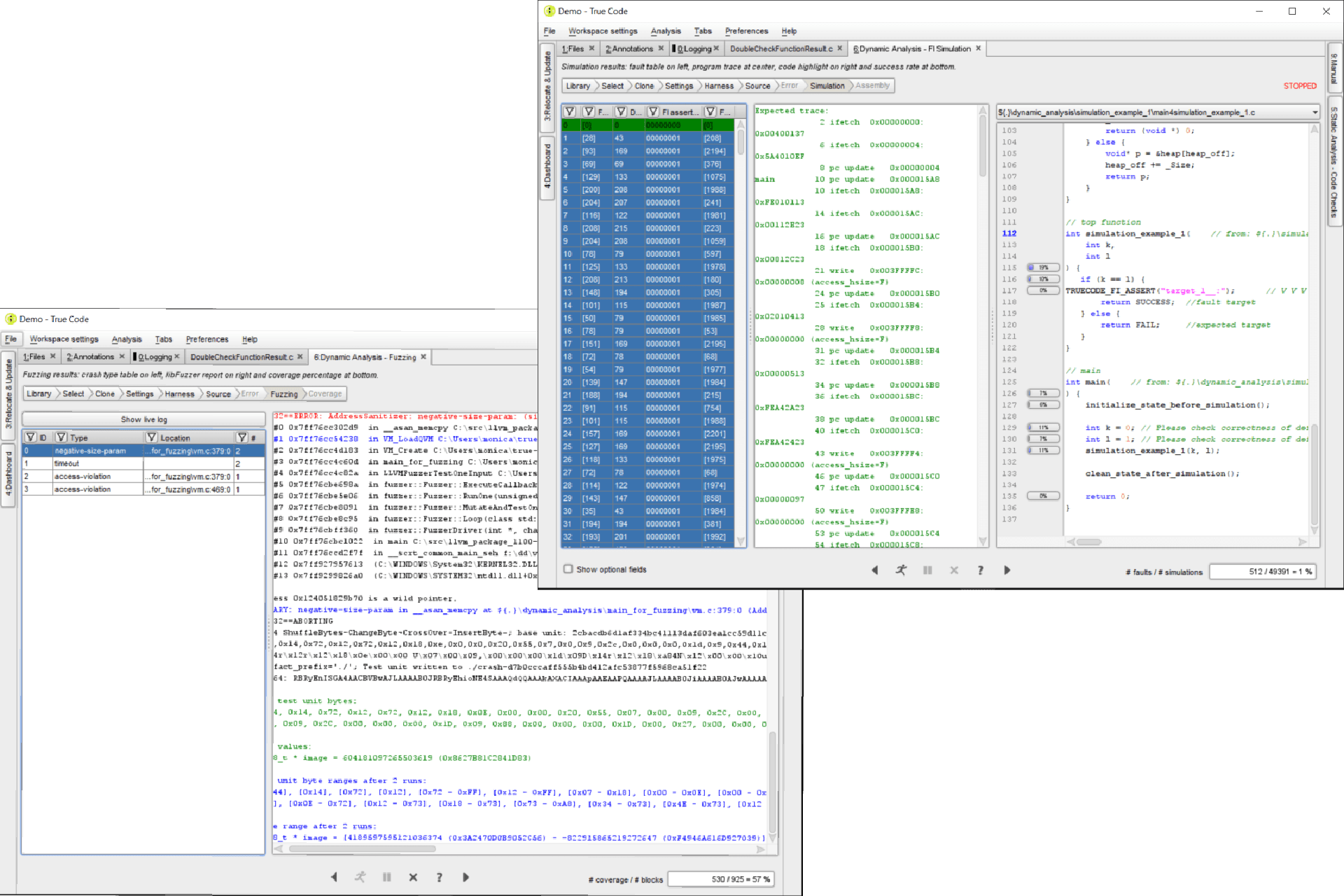
Dynamic AnalysisDynamic Analysis is a testing method that we use to provide actionable feedback and the precise location in the C code where a security vulnerability exists. We use two methods to check for vulnerabilities at runtime: Fault Injection simulationThis method simulates fault injections in the target architecture (Risc-V, Arm, or bespoke RTL) and discovers undesired behavior. FuzzingThis method increases robustness of your code by exhausting potential inputs to the functions, potentially leading to security breaches and crashes. Therefore it discovers unexpected behavior at runtime in vulnerable interfaces. |
 |
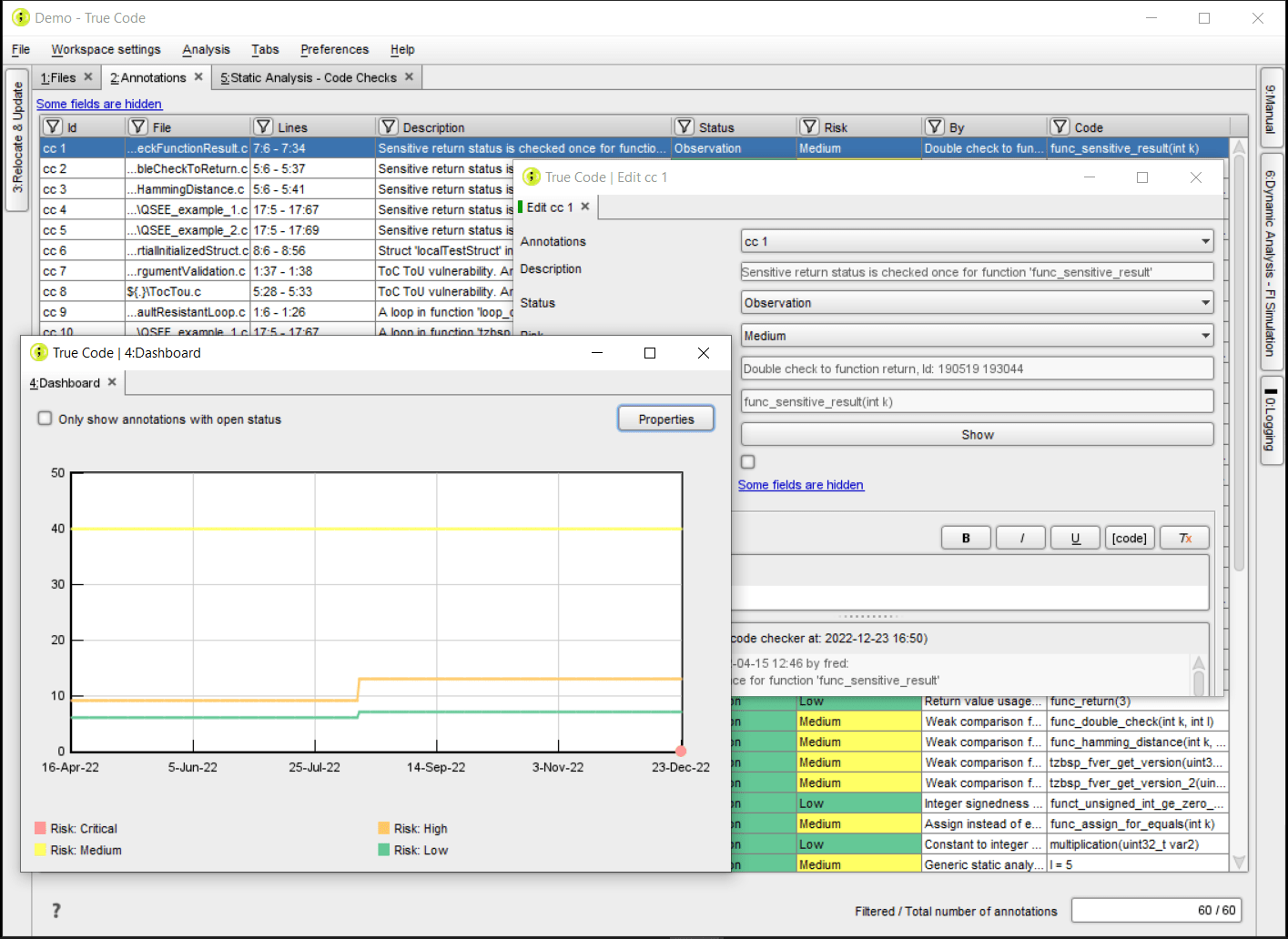
CollaborationWe enable a natural collaboration between security evaluators and the development team during the entire development process. The collaboration feature helps your team to easily track, organize and resolve those findings in a timely manner. The result is reduced development time and certification costs. |
 |
Mitigation assistanceMitigation of the security risk should be part of any development process. For the embedded software development process it is especially important to comply with the standards. In this way, developers get direct feedback on the code and can quickly start with the mitigating actions. |
 |
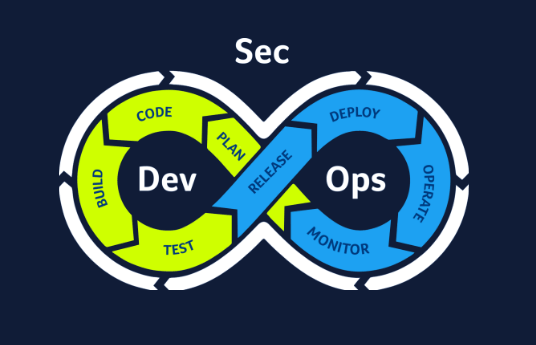
DevSecOpsFinding security vulnerabilities and issues during the development phase and immediately resolving them can be up to 100 times cheaper compared to doing the same later in the process. We bring this promise of shifting to the left within reach through tight integration in the SDLC, sharing discovered vulnerabilities instantly with all team members. |
 |
True code datasheet
Riscure True Code 2023.1 Release
New feature: Benchmarks
We completely redesigned packaging of fuzzing and fault injection simulation in the form of benchmarks. The redesign integrates the dynamic analysis
into a typical development workflow, enabling continuous monitoring of security vulnerabilities in C projects.
Hardware abstraction for FI Simulation
In this release you will find a new hardware abstraction layer (HAL) to enable custom mock implementations of memory-mapped devices. Using the HAL instead of source code stubbing, you can simulate code that directly accesses hardware addresses without modifications to source code.
Server API
The new True Code API server allows you to setup a central space for these diagnostic on your network. With the server, we release Java, Python, and Javascript clients to enable custom integration of True Code’s diagnostics into your ticket system or to script reporting, even on workstations or servers that do not have the True Code toolchain installed.
True Code for automotive
The ISO/SAE 21434 heavily emphasizes risk identification methods and establishes processes to address security risks. Automotive Safety Integrity Level (ASIL) is used for the classification of the hazards. The distinction between unintended (safety) risks and intended (security) risks has not been made in this standard. It goes without saying that vehicles cannot truly be safe if they are not also secure.
Modern vehicles can have up to 100 Electronic Control Units (ECUs in them depending on their class, make, and model, with the number of ECUs rising even higher in the case of electric vehicles. Each ECU has embedded software running on them. Mitigation of the security risk should be part of the embedded software development process to comply with the standards.
Managing cyber security risks in Automotive is done with Threat Analysis and Risk Assessment (TARA). In this model, the threats are identified and mitigating actions are determined. With True Code, you will have a complete implementation for the development and test phase in the TARA model. From static and fault injection code checks to fault injection simulation and Fuzzing at runtime.
True Code for IoT
Connected IoT devices comprise many parts from different manufacturers. This creates a complex ecosystem of manufacturers and suppliers that need to prove the robustness and the hardening of security vulnerabilities of their products. Although security guidelines like SESIP and PSA Certified are helping to address the IoT security challenge, it is not nearly enough to protect these devices against malicious intentions. IoT devices are inexpensive, accessible, and can be physically tampered with, making them an easy target for hackers.
From that perspective, it makes sense to make sure that the embedded software running on that device has no vulnerabilities. Measures are taken with secure elements, asymmetric keys, and digital certificates, but it is also important to make sure that glitches in the hardware do not result in code being skipped and therefore undo the countermeasures.
True Code does specific embedded software and firmware code checks to make sure that the code is not vulnerable to hardware Fault Injection. By simulating fault injection on the target architecture the behavior of the software at runtime is tested and feedback is supplied to take mitigating actions. Interfaces can be tested at runtime by using our automated Fuzzing. All these checks are automated in the development and DevOps process to make sure that the complete code base is checked and regression testing is done each time when new code is submitted.
Request a free trial
Feel free to contact us anytime at inforequest@riscure.com or fill out the form below.
Support Portal
Tutorials, manuals, FAQ, release notes, software updates, issue tracking and much more can be found on our support portal. Please sign up and login at: https://support.riscure.com/
An annual user workshop
We organize an annual user workshop where we present the latest developments in side channel analysis and fault injection testing and provide practical tips. The User Workshop is free of charge. Learn more about last years: https://www.riscure.com/riscure-workshop-2022/
Dedicated support
We have a full-time support team to help with any issues you might face while doing your work. Our skilled people will try to get you back on track as fast as possible.
For technical assistance call +31 (0) 15251 4090 or visit our support portal.


