Secure boot bypassed
Secure boot is under constant attack and therefore bypassed on embedded devices used across industries. Whether bypassed using software vulnerabilities or using hardware attacks like fault injection as we and others have previously shown. Secure boot is paramount for secure embedded devices as it prevents malicious actors from obtaining persistent runtime control. In this talk, we present our vision on secure boot design for embedded devices by means of clear, concrete, practical and easy-to-follow recommendations.
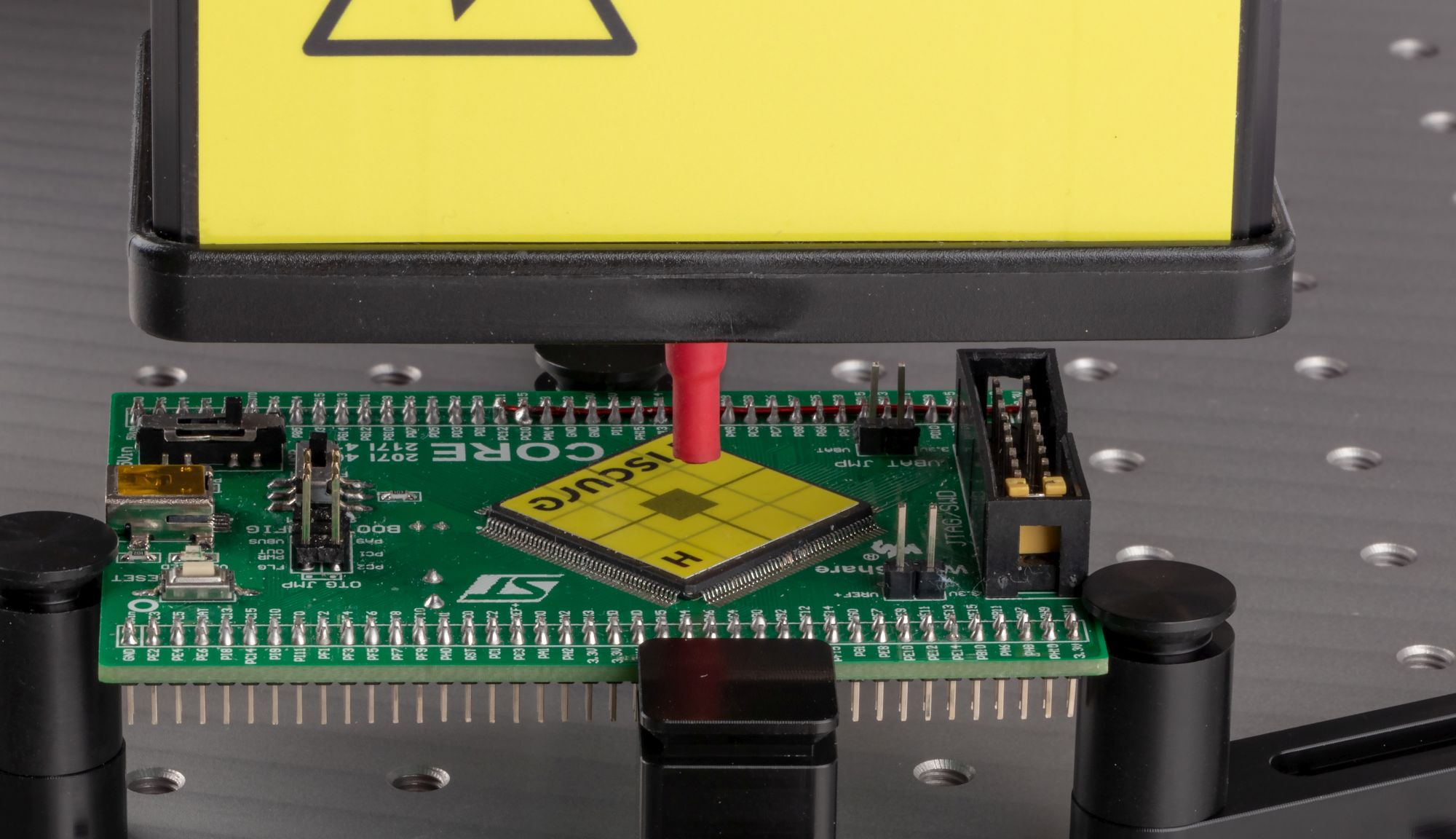
Fault injection demonstration
We leverage our decade-long experience analyzing and bypassing secure boot implementations of embedded devices used by different industries. We understand, in order to be realistic, we need to consider secure boot’s functional requirements, engineering costs, and other non-security related requirements. Where possible, we use practical examples that are easy to follow and implement. To keep it fun, we will have a fault injection demonstration live on stage where we bypass secure boot on a fast and feature-rich chip. The audience will be able to follow up on the discussed topics with two white papers which will be released after our talk.
Download slides here or view them below.