The recent IOActive DJI Mavic 2 FI drone attack serves as a testament to the evolving landscape of cybersecurity threats. This article aims to highlight the Riscure tools utilized during the IOActive DJI Mavic II FI drone attack and will explain the role each of these tools played in contributing to IOActive’s success and the value they added to the project.
XYZ Stage:
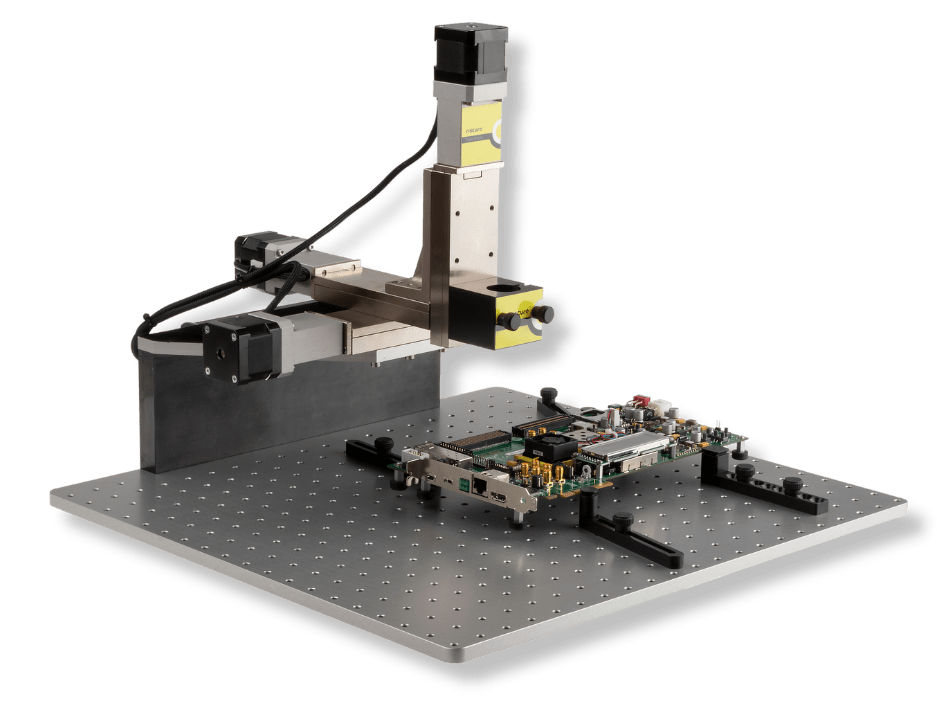
This tool was used to mount Side-Channel Analysis (SCA) and Fault Injection (FI) tools, facilitating the scanning of the chip’s surface with exceptional accuracy. The XYZ Stage’s accuracy combined with Inspector Software gives the ability to identify optimal spots on the chip where information leaked, was crucial in the pursuit of cryptographic keys.
Its precision laid the foundation for subsequent steps in the operation. By offering a stable and repeatable platform, the XYZ Stage ensured that data acquisition remained consistent and reliable throughout the project, minimizing the margin for error and optimizing the chances of success.
High Precision EM Probe:
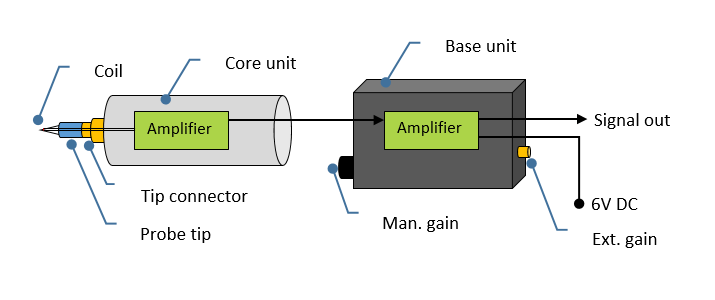
In the quest for cryptographic keys, the High Precision EM Probe proved to be a valuable asset. Positioned over the System-on-Chip (SoC), this probe recorded thousands of traces to detect leakage from electromagnetic emanations. The HP EM Probe is equipped with 3 tips of varied diameter (0.2mm, 0.5mm, and 1.2mm), allowing security testers to scan different areas & resolutions on the target.
The High Precision EM Probe’s sensitivity allowed it to capture the variations of electromagnetic emissions very accurately (up to 6GHz depending on which oscilloscope used). This ability to record thousands of traces, combined with its flexibility in detecting a broad range of frequencies, was valuable for IOActive. By converting these traces into actionable data through the Inspector software, the team was able to pinpoint vulnerabilities and fine-tune their approach with precision.
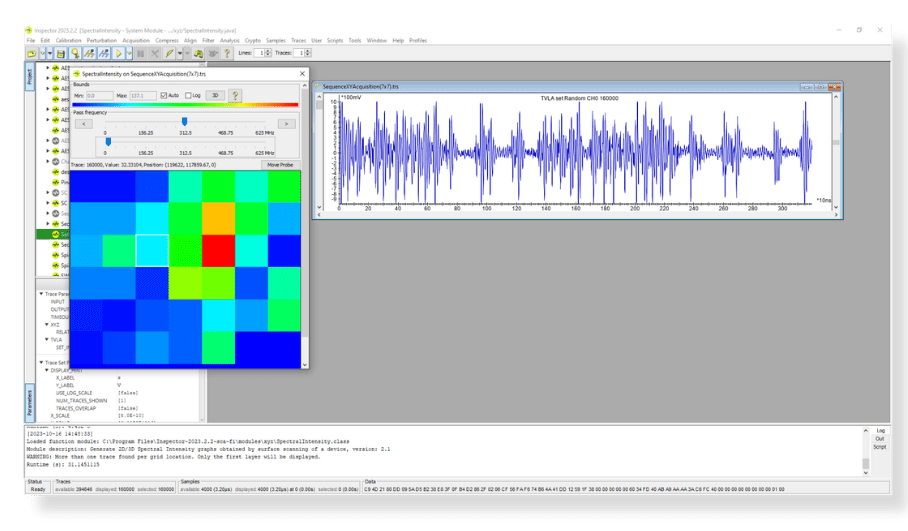
Coupled with Riscure’s Inspector software, it visualizes these frequencies into heat maps that illustrated areas of power leakage. This visual representation played a critical role in identifying weaknesses in the drone’s chip security.
EM-FI APW & Spider:
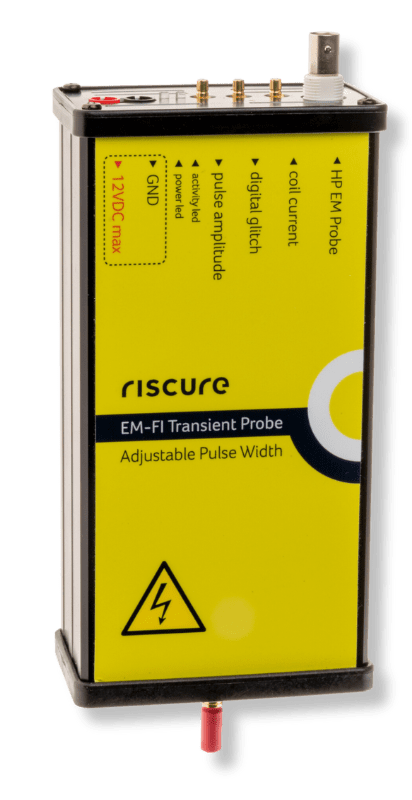
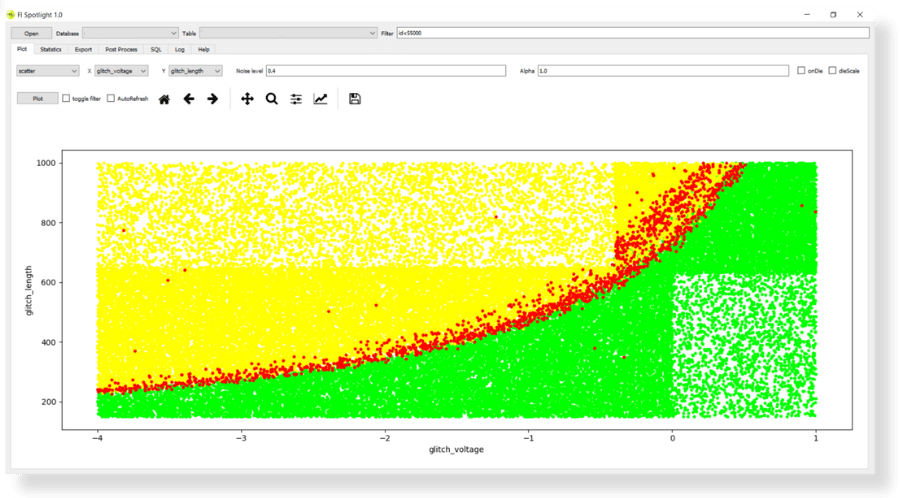
IOActive’s use of the EM-FI APW Probe and the Spider for fault injection attacks allowed for precise control over electromagnetic pulses induced in specific areas on the DJI target. This combination enabled exact manipulation, with control over output power, timing, repetition rate, and pulse duration. Injecting glitches of varying strengths, lengths and timing, IOActive ultimately observed the glitches that led to the dji_verify program’s crash, exposing critical vulnerabilities.
The EM-FI APW Probe and the ‘Spider’ became the tools that allowed IOActive to act with surgical precision. By adjusting the electromagnetic pulses in a controlled and calculated manner, the team was able to uncover vulnerabilities without causing unnecessary disruption. What set this tool apart is its ability to measure EM signals simultaneously (to find the correct point to inject the glitch) while glitching the target, as well as, controlling the pulse width being emitted. The variable pulse width not only expands testing options but also enhances accuracy and efficiency, eliminating the need to switch devices for separate measurements and to identify the optimal test location for a Fault Injection attack. The ability to observe and learn from the glitches was essential in understanding the system’s weaknesses and crafting an effective strategy.
Riscure’s Inspector Software:
Much like an orchestra director, Riscure’s software played a significant role in coordinating the various hardware tools. It directed the SCA and FI hardware tools when to acquire traces or initiate glitch injections. Riscure’s Inspector software comprises several modules designed for post-processing traces, including filtering, alignment, and compression. This post-processing capability was vital for analyzing leakage through first-order analysis, known key analysis, or known key correlation. The software also facilitated the visualization of Fault Injection outcomes and assisted in selecting the most effective glitch parameters for a successful campaign.
Riscure’s software’s Safe post-processing capabilities allowed the IOActive team to transform raw data into actionable insights. By filtering, aligning, and compressing traces, the team could dissect the security of the DJI target systematically, enabling them to make informed decisions and plan their next steps with confidence.
In conclusion, the success of IOActive’s mission to compromise the DJI drone reinforces the significance of meticulous security testing. By doing so, it’s important to have the right equipment for the job. Riscure’s hardware testing tool suite is the industry standard for testing the security robustness of your products. For more information, please don’t hesitate to reach out to inforequest@riscure.com. Together we can collectively strengthen defenses and promote a more secure technological future.