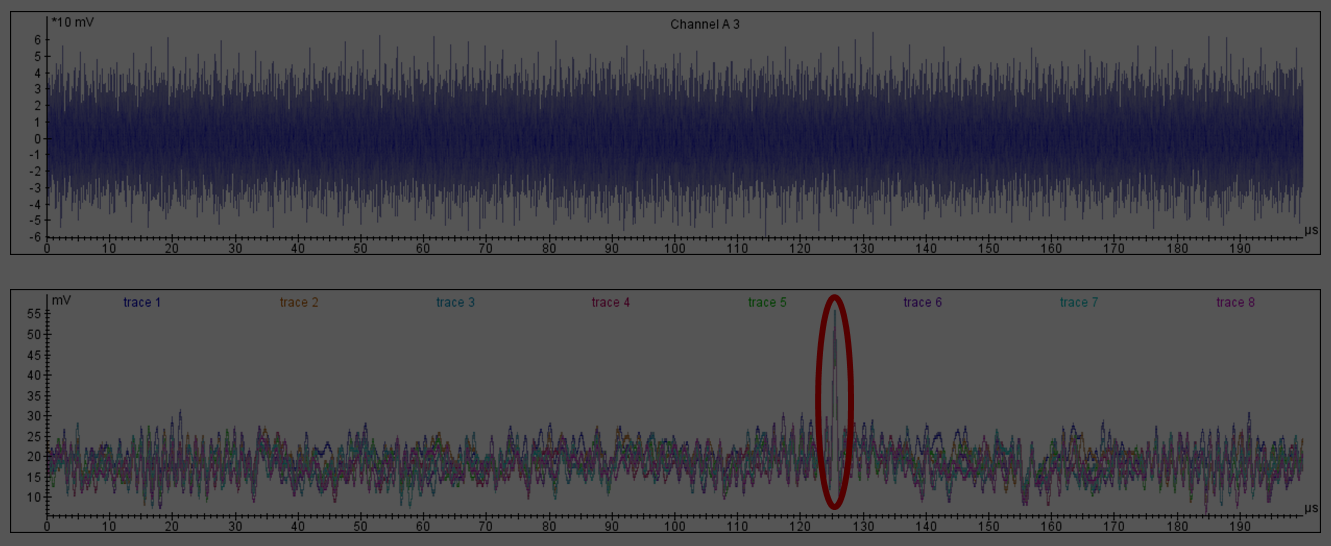
Side Channel Attacks
Side channel attacks target the unintended (and therefore often unsecured) channels of communication. This often requires physical access to the device, making consumer devices with a security function and access control tokens ideal targets.
Some of the most commonly attacked side channels are:
- Time: the time needed to complete certain operations.
- Power: the power available to and used by a device.
- Electromagnetic radiation: EM radiation produced by a device.
Defensive Patterns
This paper divides the patterns designed to secure against various attacks into two groups: those against data leakage and those again fault injections. The patterns used to counter data leakage focus on protecting confidential data like keys and passwords as well as hiding sensitive decisions. Patterns focusing on fault injection aim to protect critical data or program flow. Before implementing any of these patterns, a developer should consider the risk of a side-channel attack. For example, is there a reason an attack might be attempted, are the side-channels the most obvious weakness in the device, and is it even possible to get physical access to the device? If the answer to these questions is ‘Yes,’ then a series of steps should be followed to protect the device.
- Understand the hardware and operating system’s resistances
- Identify the potential weaknesses in the application design
- Implement the appropriate patterns
- Test the device and security
Download the free whitepaper now