Riscure’s researchers analyzed more 426 Android payment applications, downloaded directly from the Google App Store. The selection was made based on the Host Card Emulation functionality. Implementation of this technology directly indicates that an application is likely to be used for mobile payment (and not only for mobile banking, for example, where transaction security is not always required). Riscure has a lot of experience analyzing payment apps manually, utilizing methods such as source code review, penetration testing, and vulnerability assessment. In this research Riscure Touchstone, an automated tool currently in development was used to analyze applications.
In its current form, Riscure Touchstone looks for a wide variety of indicators that signal the existence of a certain security technique being implemented in an application. These indicators can be grouped into six major categories of techniques that make an application more robust against malicious actions. These six categories are anti-analysis, anti-rooting, anti-instrumentation, anti-tampering, anti-cloning, and anti-key recovery. Of course, each of these approaches can be implemented in many different ways. Our developers have successfully solved the challenge of reliably detecting the implementation of the most widely adopted security algorithms in the code of an Android application.
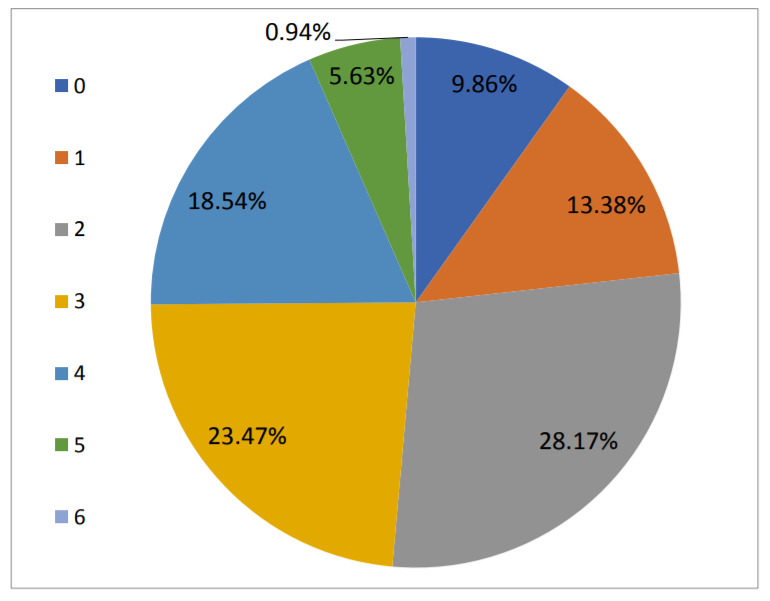
The results are far from optimistic. Less than 1% of applications were found to use all six security approaches, and approximately 10% of applications apparently do not use any countermeasures at all. Among security features, the Anti-Rooting capability is the most frequently used one, found in 78% of applications. The most rarely used capability is Anti-Cloning, it was detected in 9.2% of applications. Additional findings with the detailed description of security features can be found in this whitepaper.
Does this mean at least 10% of payment applications are critically vulnerable and put customers or financial institutions at risk? Not necessarily. The goal of the research was not to identify vulnerable applications but to analyze the functional capabilities of mobile payment apps. It is possible that mobile apps with zero or one security features actually ‘hide’ a custom security algorithm within their code – a practice by itself sometimes questionable. Although directly looking at an application ‘from an attacker’s perspective’ is what actually offers a developer objective data, automated evaluation of security properties could be the first step to recognize where a software solution stands in terms of security robustness, and what could be improved.
It is possible to test your mobile payment applications via a beta-version of Riscure Touchstone here. To obtain an invite code, please contact us via the form below or send a message to inforequest@riscure.com. You can learn more about Riscure’s security offer for Mobile Banking here.