Designing Secure Bootloaders
Riscure Academy - Online Group TrainingFor architects, designers, and developers of bootloaders to learn how to deploy security best practices to develop/harden bootloaders.
Duration
4 courses
4-6 weeks
24 hours self-paced eLearning
6 hours Live Mentoring
Certificate
80% or higher on final assessment
Team report (pre vs post assessment)
Interactive
Exercises
Assignments
Quizzes
Live mentoring
Scalable
Self-paced eLearning
Scheduled live mentoring
Spaced for efficiency & effectiveness
Scale to multiple groups
After this program participants will be able to
Explain & describe:
By having foundational knowledge of what the design building blocks are for secure boot, and understanding a variety of state-of-the-art threats, participants build the competencies and more importantly the confidence to tackle difficult decisions head-on.
Analyze trade-offs and make decisions:
Being able to determine the cost vs. benefit of each of the building blocks of a secure bootloader is the first step to empower developers to building with security awareness top-of-mind and making the best choices of what countermeasures to introduce for your particular use case.
Implement & harden:
Through a series of practical examples and exercises participants are guided through identifying vulnerabilities, implementing from scratch, all the way through to hardening a faulty bootloader. This highly practical way of learning by doing will give developers the best foundation to apply their knowledge in their work.
Designing Secure Bootloaders
This program helps architects, designers, and developers of bootloaders become aware of common security mistakes and teaches how to correct or avoid these in a highly practical way.
Most embedded devices have strong requirements on the integrity of the code running on the platform. Attackers are finding new ways to compromise these systems. A robust secure boot implementation that ensures software integrity is considered essential. Implementing a robust secure boot is a major challenge. Several attacks of widely deployed embedded devices received high profile media attention, exposing manufacturers to lost revenue, liability claims and brand damage.
What makes this program unique?
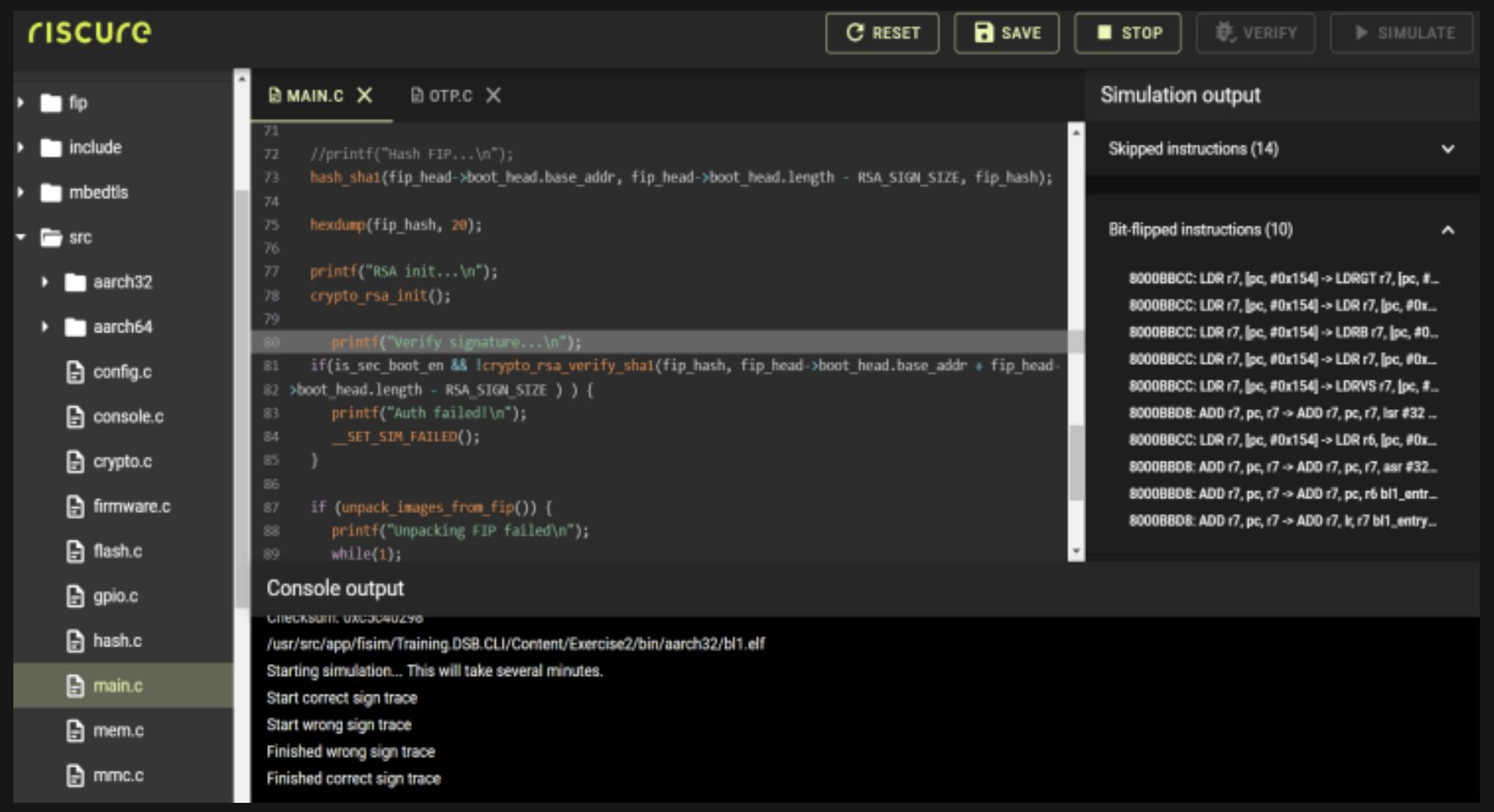
This is the first program aimed at developers where we transform an existing bootloader into a secure bootloader. Highly practical exercises are done in a virtual practice environment, the Fault Injection Simulator, where the participants applies the learned concepts to secure a generic implementation of a bootloader. The version provided is a functional bootloader that contains the top 10 security mistakes we see in a typical implementation of a secure bootloader.
Architects, designers, and developers of bootloaders
Analyze implementation trade-offs
Implement a secure bootloader
Harden a bootloader
Secure Bootloader Fundamentals
- Anatomy of a bootloader
• Design requirements
• Implementation requirements
• Secure chip platform, secure software, cryptographic primitives - Threat analysis & risk assessment fundamentals
• Asset, threat, vulnerability, practical security, risk
Secure Bootloader Building Blocks
- Hardware (ROM, OTP)
- Cryptography
• Confidentiality, integrity, authenticity
• Cryptographic schemes
• Symmetric vs asymmetric crypto - Bootloader code
- Product Lifecycle
Common Pitfalls: Software
- Analyzing a bootloader
- Assumptions & logical flaws
- Software flaws
- FI Simulator Exercises: software flaws, source code review, writing a secure bootloader
Common Pitfalls: Hardware
- Hardware attacks
- Fault Injection attacks
- Combined attacks
- Countermeasures
- FI Simulator Exercises: identifying single points of failure, hardening a secure bootloader
Lead developer

Name Here
Actionable and indispensable knowledge of security in Embedded Systems and IoT devices. Training on hardware and software security in a classroom setting, online or hosted in your own knowledge program.
What people say
“Very interesting learning approach and material across different aspects of state-of-the-art SoC development with Security in mind. I really want to thank Riscure for offering such good trainings, and the their trainers who make amazing use of their skills, experiences and kindness to easily communicate complex concepts to the audience.”
– Qualcomm
Get Started Today
Don’t let your organization’s embedded systems become an easy target. Invest in the security and success of your business by partnering with Riscure Academy. Contact us today to discuss your training needs and explore our approach. Together, we’ll empower your team to secure your organization’s future.
Frequently asked questions
Do you do individual training?
Individual training is available for self-enrollers within enterprises, but we do not training for individuals outside of organizations. For individuals we recommend Self-Paced or Open training. If you are unsure, please get in touch by filling in the form below.
What is the minimum group size for your expert-led training program?
Are your programs delivered online or as classroom ?
customer's location. Our online programs blend self-paced e-learning, exercises, assessments, and in certain cases expert-sessions (like Q&A webinars or Group Exercises) with Riscure experts.
When can we start with the training/ what do the training schedules look like?
We do not have pre-defined dates for our training sessions. Instead, we aim to accommodate your preferred start time and schedule the spacing of training and relevant sessions accordingly. To ensure a seamless scheduling process, please provide advance notice of 3-4 weeks for our online group programs and 6-8 weeks for classroom programs, as this allows us to secure our trainers' availability. For online training by individuals (self-paced) any enrollment will be facilitated within days or weeks, depending on the level of integration with the customer training platform or HR system. For Open Training schedules, please, contact us by filling in the form below.
Does customer have access to the training materials after the program?
For expert-led group training, including online/hybrid and classroom formats, access to relevant training materials remains available after the training period. The formal training schedule with deadlines is coordinated between Riscure and the customer.