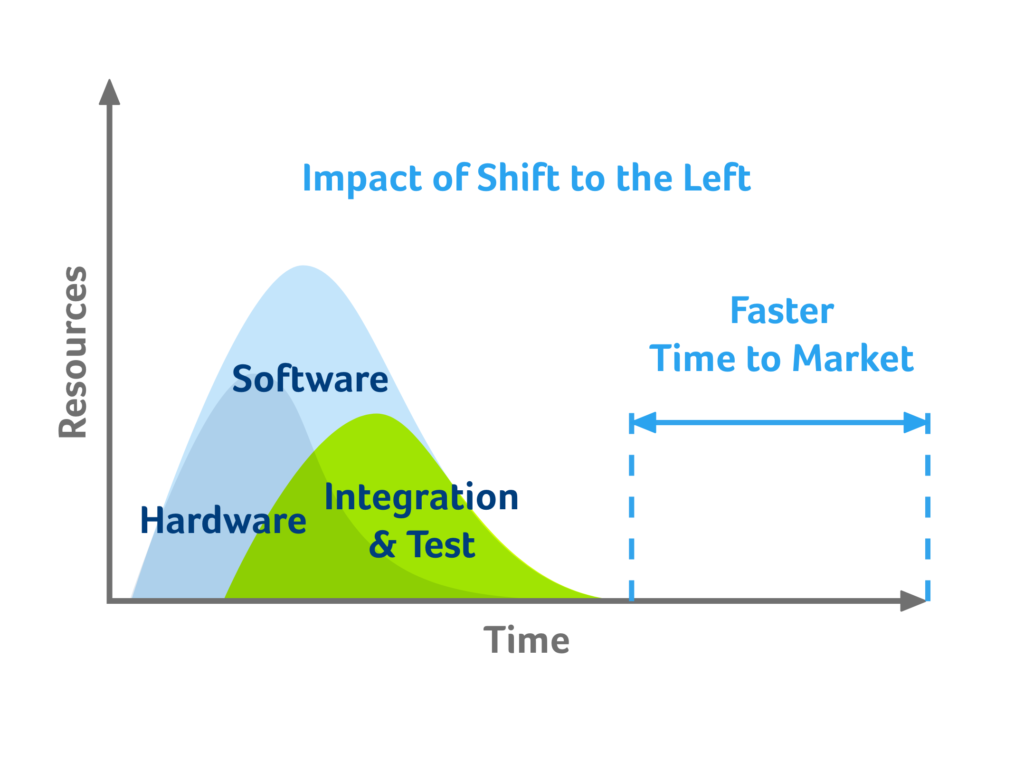
Shift to the left
In the past, the role of security was isolated to a security team in the final stage of development. That wasn’t asbproblematic when development cycles lasted months or even years, but those days are over. Effective DevSecOps ensures rapid and frequent development cycles (sometimes weeks or days). Outdated security practices can undo even the most efficient development projects. Make the shift to the left and integrate security in your daily CI/CD build and discover security issues earlier in the process and save time and repair costs.
Integrate security in the sSDLC
Developers and security specialists colaborate
For integrating security in the SDLC it is important that security analysts and developers can communicate in a clear and easy way. Developers are not security specialist and need clear feedback on the vulnerability issues and how to mitigate. True Code has a database with feedback directly to the code where annotations can be made also for future reference.
Because of its close collaboration with the Riscure Lab, True Code has far fewer false positives than other code checkers. Even false positives must be checked in Triage to see if they are really false and explained why, so fewer false positives results in less time wasted.
By integrating True Code in the daily build you can include security testing in your continuous integration (daily build) and run the automated security test on your complete code base. This will improve the security of the entire process and also offers more peace of mind than a random manual code check that is often performed when automated security testing is not implemented.
The feedback reports of the True Code database also provide an excellent starting point for QA or certification. With the complete code coverage it is easier to identify code slices that need extra attention and the certification can be done much faster.
Static Application Security Testing (SAST)
With True Code for Static Application Security Testing (SAST) or White Box testing we provide all the logical and fault injection static checks. Coding standards and best practices of Mitre and OWASP are implemented in the logical static code checks. We have extended this with all the checks that the Riscure Lab has developed over the years and specifically for embedded sfotware and firmware we have added checks for Fault Injection attack mitigation.
Dynamic Application Security Testing (DAST)
Only SAST code checks are not enough to get a secure embedded software solution. Fault injection in the hardware can cause the software to behave in an undesired manner, which is why it is necessary to check for vulnerabilities while the software is executed. True Code has two options to check for vulnerabilities at runtime, Fault Injection simulation and Fuzzing. These two methods of Dynamic Application Security Testing (DAST) are described below.
Fault Injection Simulation (DAST)
True code can simulate the target architecture and introduce glitches into it to simulate a Fault Injection attack and measure the behavior of the software. By running the software repeatedly on the architecture and introducing glitches the behavior is measured and any undesired behavior reported. True Code gives direct feedback in the code that is responsible for the unexpected behavior and mitigating actions can be taken by the developers. Currently, the Risc-V and Arm architectures are supported, which covers a large part of the market, but other architectures can also be supported even before they are put into production. This requires the RTL and the Netlist (Verilog) of the target architecture but we offer a DIY solution so you do not have to expose your IP.
Fuzzing (DAST)
With Fuzzing True Code exhausts communication variations to identify unexpected behavior. Fuzzing is a Black Box software testing technique, which basically consists in finding implementation bugs using malformed/semi-malformed data injection in an automated fashion. Interfaces can be vulnerable for this type of testing. True Code gives direct feedback about the interfaces that are vulnerable and mitigating actions can be taken. You do not need to make unit tests and test scenarios to test your interfaces. True Code Fuzzing creates all tests and scenarios for you and saves many hours of manual labor.
SAST and DAST in DevSecOps
True Code is the only security code analyzer for embedded software that uses both SAST and DAST to find vulnerabilities. By using True Code in your DevSecOps process you will get a complete coverage of your code base and peace of mind that the code is secure both before and after execution. Research shows that an exploit is based on an average of 3 simple vulnerabilities. By using True Code the risk of an exploit is drastically reduced. Manual code checks are still required but by using True Code focus can shift to the truly important pieces of code.

True Code Datasheet